IT Security
Security and Operations Team
The cyber security program at Larimer County IT aims to address Confidentiality, Integrity and Availability, also known as the CIA triad, of digital assets at Larimer County. Confidentiality aims to be sure the right people have access to the right information. Integrity of data means that it hasn't been altered in an unauthorized way during its lifecycle; maintaining accuracy of data and enhancing its trustworthiness. Availability of data means the hardware and software (i.e. servers and storage) are functioning properly and the data can be successfully accessed.
Larimer County IT employs several tactics to ensure all three facets of the CIA Triad are achieved. These include deploying a comprehensive anti-virus solution, robust firewalls, redundant storage solutions and proper data encryption to ensure Larimer County services remain available to our citizens.
The following five functions are used to foster an operational culture that is aware of, and dynamically adapts to, cybersecurity risk.
- Identify – Develop the organizational understanding to manage cybersecurity risk to systems, assets, data, and capabilities.
- Protect – Develop and implement the appropriate safeguards to ensure delivery of IT services.
- Detect – Develop and implement the means to identify the occurrence of a cybersecurity event.
- Respond – Develop and implement the actions required to deal with a detected cybersecurity event.
- Recover – Develop and implement resiliency plans and to restore any capabilities or services that were impaired due to a cybersecurity event.
Partnerships
Larimer County has made strategic technology investments that enables the delivery of high-quality services to our citizens. We are equally invested in protecting these technology assets from current and future threats. To that end, we continue to strengthen our collaborative relationships with Federal, State and Local agencies to enhance our mutual protection and ensure reliable, secure and effective services.
Two such agencies are the Multi-State and Elections Information Sharing & Analysis Centers. These partnerships provide us with the necessary resources to help keep critical County operations available.
Online Security
Web Encryption
Every page, form and document hosted on larimer.org is encrypted - meaning visitors can trust a secure connection between their browser and our site when browsing pages or completing a form on larimer.org. When visiting an encrypted site note the lock icon, near the web address:
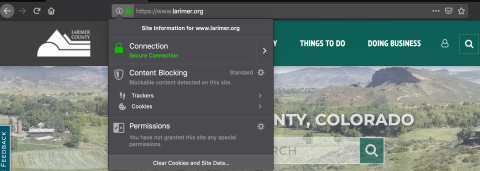
We work especially hard to maintain high levels of encryption, and for our efforts have attained an A rating on Industry standard Qualsys SSL Labs Site Review:

(You can view our real time rating on SSL Labs Site)
Secure Site Hosting
Our current web platform provides:
- Container-based infrastructure
- Automated, one-click core updates
- Denial of service(DDoS) protection
- Automated security monitoring
- Network intrusion protection
- Automated HTTPS
-
Vulnerabilities and Incident Response
- SAML/SSO/2FA
- Role-based change management
- Automated backup and retention
- Secure code and database access
- Secure integration to resources
- Secure datacenter
-
Privacy Shield & US-Swiss Safe Harbor Certified
Vulnerability Scans
In addition to encryption, we monitor our site monthly for security vulnerabilities and weaknesses using industry leader and third party Trustwave.




